lunes, 28 de noviembre de 2011
Networking test in NachOS
In order to make a networking functionality test in nachos we must first open two separate terminals, then we enter to the network folder, after we enter we must write ./ nachos. When we finish writing ./nachos we write first -m 0 (from) -o 1(to) in one terminal and then -m 0 (from) -o 0 (to) in the other terminal simultaneously.
Now where we wrote -m 0 -o 1 we will receive this message:
Got "Hello there!" from 1, box 1
Got "Got it!" from 1, box 1
Machine halting!
Where we wrote -m 0 -o 0 we will receive this message:
Got "Hello there!" from 0, box 1
Got "Got it!" from 0, box 1
Machine halting!
Now where we wrote -m 0 -o 1 we will receive this message:
Got "Hello there!" from 1, box 1
Got "Got it!" from 1, box 1
Machine halting!
Where we wrote -m 0 -o 0 we will receive this message:
Got "Hello there!" from 0, box 1
Got "Got it!" from 0, box 1
Machine halting!
Here we show you some of the code in nachos that does this
This is contained in nettest.cc
Here it sends a message to the machine with ID "farAddr", then it waits for this message to arrive. When it sends an acknowledgement for the other machine´s message it keeps waiting for the acknowledgment from the other machine to the original message.
Now we construct the packet and we specify the destination where we are going to send it, and also from where we are sending the packet.
Finally we send the message and we wait for a confirmation message from the other machine.
The execution would be like this:
Network in Nachos
Here we are going to show you a little introduction of how networking works in NachOS.
In Nachos we have two main classes:
The network class
The postoffice class
Network
The network class is not directly used by the user. It is the Link between nachOS and sockets TCP/IP.
It has four methods:
- Send: Sends a packet to a NachOS machine.
- Receive: If there is a packet, it receives it. If not, it returns with a 0.
- CheckPktAvail: It activates regularly to verify if a packet arrives.
- SendDone: When it receives the packet, it calls a manager in order to organize it.
For communication, NachOS uses PacketHeader and MailHeader.
They both contain:
To (Destination of the packet)
From (Origin of the packet)
Length (Size of the packet)
Postoffice
Example of postoffice
- Sends a packet to a given address
- Waits for a message and prints it once received
- Sends another packet to the same address
- Waits for a message and prints it once received
Now we are going to explain some other important files in the network folder and we are going to show you some code
- nettest.cc (nachos/code/network)
Here is where we run the routines of the network test.
- post.h, post.cc (nachos/code/network)
They help to synchronize the data sent and received. (like a messenger)
Here we show you some code
Post.h
Post.cc
- network.h, network.cc (nachos/code/machine)
They are a physical network hardware emulation.
Network.h
Network.cc
References:
bit.ly/vtlhRr
bit.ly/vtlhRr
domingo, 27 de noviembre de 2011
Wireshark
Ok, in the last publications many people talk about encrypt, security, pings, and other, but we need to know a some tools that can help to want vulnerabilities in ours network, for example the information that we send and pass to the modem or other computer, this information is encrypt or go visible? or how many package we send and what package we send.
For this things have a many tools for example, nmap (this help to know the network, ports, information of the computer connected in the local network), aircrack (help to decrypt the key of the router or modem), kismet (help to put the network card in mode monitor "sniff"), wireshark(sniff packages).
But and talk about wireshark, is a tool using to make testing in the network
We can download putting in terminal sudo apt-get install wireshark
Then we run in mode administrator (sudo)
Then we go in Interface List and choose wlan0
 Next the program open a window showing the package that was sending
Next the program open a window showing the package that was sending Then of a little time, we stop the program.
Then of a little time, we stop the program. Stop listening and you will see the information, for example where is the place to go and what your destination.
Stop listening and you will see the information, for example where is the place to go and what your destination.
If we click on one of them we will display all your specific information,which is where you used that port, protocol, etc.
 Also what can be done is that you give and give it the 2nd buttonFollo TCP Stream and teach you the information being sent.
Also what can be done is that you give and give it the 2nd buttonFollo TCP Stream and teach you the information being sent.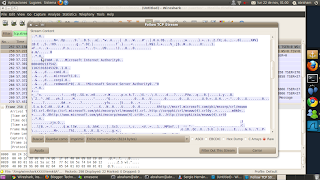 If we try to read it, we can not, as many times this is encrypted, so you will not see, rather than the odd line.
If we try to read it, we can not, as many times this is encrypted, so you will not see, rather than the odd line.But now we know how this works, seen with the previous, so we can implement any tool or program to unzip us the information. For this too has wireshark decryption tool, it is a matter of us to choose which is the indicaga as they deal with different protocols. To facilitate thiswe can also set filters, that is which at a certain port and ip.
Client - Server
Here is the code of client-server using a simple chat and implement encrypt text or you can download the code in this links: server.py and client.py
#!/usr/bin/python
# Server program
from socket import *
# Set the socket parameters
host = "localhost"
port = 21567
buf = 2048
addr = (host,port)
# Create socket and bind to address
UDPSock = socket(AF_INET,SOCK_DGRAM)
UDPSock.bind(addr)
#decrypt
def decrypt(a):
length = len(a)
for position in range (length):
temp = ord(a[position])
temp = temp - 1
temp = chr(temp)
data = a[:position] + temp + a[position + 1:]
return data
print "Waiting message..."
# Receive messages
while 1:
data,addr = UDPSock.recvfrom(buf)
data1,addr = UDPSock.recvfrom(buf)
if not data:
print "Client has died!"
break
else:
data, key = data.split(';')
print "\nReceived message '", data1,"'"
clave = raw_input('Give me the key to decrypt: ')
if (clave == key):
decrypt(data1)
print "Mensaje: ",data
else:
break
# Close socket
UDPSock.close()
#!/usr/bin/python
# Client program
from socket import *
# Set the socket parameters
host = "localhost"
port = 21567
buf = 2048
addr = (host,port)
# Create socket
UDPSock = socket(AF_INET,SOCK_DGRAM)
def_msg = "Write something ";
print "\n",def_msg
#encrypt
def encrypt(data):
length = len(data)
for position in range (length):
temp = ord(data[position])
temp = temp + 1
temp = chr(temp)
data = data[:position] + temp + data[position + 1:]
return data
# Send messages
while (1):
data = raw_input('Introduce Message: ')
clave = raw_input('Give me the key: ')
data = data+";"+clave
if not data:
break
else:
if(UDPSock.sendto(data,addr)):
print "Sending message.....\n"
data1 = encrypt(data);
UDPSock.sendto(data1,addr)
# Close socket
UDPSock.close()
Now i'm try to explain the code:
The next part take the parameters and data sending, then separate the string in data (Information) and key (key to decrypt the text), then we compare between key to clave and if this is correct show the message and in the last part close the socket.
Execution:
host = "localhost" port = 21567 buf = 2048 addr = (host,port)In this part we set the parameters, we can change, for example port to another, the size of the buffer, and the host, but if we change in server or client, we need to change too in the other code. The parameter is used to do a connection between client and server.
# Create socket and bind to address UDPSock = socket(AF_INET,SOCK_DGRAM) UDPSock.bind(addr)In this part we create the socket connection and bind the address, AF_INET & SOCK_DGRAM, represents the address family INET for the internet sockets.
#decrypt
def decrypt(a):
length = len(a)
for position in range (length):
temp = ord(a[position])
temp = temp - 1
temp = chr(temp)
data = a[:position] + temp + a[position + 1:]
return data
The next part, is a function of decrypt, we saw this in other publication, is the same but we use to decrypt the message.
# Receive messages
while 1:
data,addr = UDPSock.recvfrom(buf)
data1,addr = UDPSock.recvfrom(buf)
if not data:
print "Client has died!"
break
else:
data, key = data.split(';')
print "\nReceived message '", data1,"'"
clave = raw_input('Give me the key to decrypt: ')
if (clave == key):
decrypt(data1)
print "Mensaje: ",data
else:
break
# Close socket
UDPSock.close()
The next part take the parameters and data sending, then separate the string in data (Information) and key (key to decrypt the text), then we compare between key to clave and if this is correct show the message and in the last part close the socket.
TUDPSock.sendto(data1, addr)
Execution:
Encryption/Decryption
This is a program we made for encrypt/decrypt some text.
In this code, first we declare the functions Encrypt() and Decrypt(), then we ask to the user to write something and we save this text in a string variable called text, then the Encrypt method is called. In this function, the variable len gets the text length and then is a for for 0 to the lenght of the text -1 this is to read each letter of the text that user write. Then we get the ASCII value of 'c', multiply this ASCII value by 2 and set the new ASCII value back into the char. Finally insert the new value back into the text. Decrypt function returns the encrypted text into the start text.
#include <iostream>
#include <cstring>
#include <cctype>
using namespace std;
void Encrypt(string&);
string Decrypt(string text);
int main() {
string text;
cout << "Write something: ";
getline(cin,text);
string temp(text);
Encrypt(text);
cout << "Encrypted: " << text << endl;
cout << "Decrypted: " << Decrypt(text) << endl;
return 0;
}
void Encrypt(string &text)
{
int len = text.length();
char c;
string Finaltext(text);
for (int i = 0; i <= (len-1); i++)
{
c = text.at(i);
int a = (int)c;
a += 2;
if (a > 254) { a = 254; }
c = (char)a;
Finaltext.insert(i , 1, c);
}
string textEncrypted(Finaltext, 0, len);
text = textEncrypted;
}
string Decrypt(string text)<
{
int len = text.length();
char c;
string Finaltext(text);
for (int i = 0; i <= (len-1); i++)
{
c = text.at(i);
int a = (int)c;
a -= 2;
c = (char)a;
Finaltext.insert(i, 1, c);
}
string textDecrypted(Finaltext, 0, len);
return textDecrypted;
}
Execution:
domingo, 20 de noviembre de 2011
Infections

Logic bombs: A logic bomb is a program code, usually running as agenda. For example, a worker of any company decided to put a program like this, and every day at certain time or day, the program asks for a password and if this password is correct the program will continue running normally, but what happen if for any cause the worker is fired, then the program will run and ask for the password and the password will be incorrect because the other people don’t know the password, the program then will show system errors, delete files, folders.
Trojan: It is any program that is in a computer or system without being detected that’s why this name. At one point depending of how it´s programmed, the trojan will perform a specific action.
Virus: It’s a program that can reproduce itself by adding code to another program. It activates while the program containing the virus runs. Viruses also will perform a specific action depending on how it’s programmed.
Worms: This type of program automatically (unlike a virus) duplicates itself many times.
There are another terms like zombies, spywares, botnets, etc.
What is a zombie? A zombie is a program that acts sending packages, information or performing another activity defined by its programmer. It can act in different computers, not just in one, therefore, we could have a computers army realizing a specific action.
A botnet is mainly used to make DoS attacks (Denial of Service). This type of attacks are used to broke servers. They can use their computer as a proxy and all the information seen will be sended to the programmer.
At the moment a server receives a request for something, it responds.
DoS (Denial of Service)
A denial of service usually works making a lot of requests to a server, saturating its bandwidth. Now users won’t have access to it, making the server unable to answer requests.
How can we accomplish that? Sending packages to the server or the user we are going to attack. What we used to do was to send a large amount of packages, saturating its bandwidth, but now there are some protocols that won’t let us do it, therefore what we now do is to infect some computers, so that they can be sending packages or making a lot of requests.
For example, if we have a brother or a friend that is all day watching videos in youtube, downloading music, using out network and making it slower, what we can do is to send them some pings. Now he’ll start to see its internet slower because we are saturating its bandwidth. We must know that by doing that, we are also affecting out bandwidth so it is recommended to use more computers when we are making this kind of attacks.
References
Cryptography
Cryptography is responsible of taking text or a file, known as plaintext, and convert it to ciphertext so that only authorized people know how to turn it back into plaintext.
Encryptation definition:
Encryptation definition:
C = E (P, Ke)
where:
C = ciphertext
E = encryption algorithm (function)
P = plaintext
Ke = encryption key
Ciphertext is obtained by using the encryption algorithm E, with the plaintext P and the encryption key (secret) Ke as parameters.
Kerckhoffs’s principle states that all the algorithms must be publics and the secret must be only in the keys.
Decryption definition:
P = D (C, Kd)
where:
D = Decryption algorithm
Kd = decryption key
To obtain the plaintext P from ciphertext C and the decryption key Kd you have to run the decryption algorithm D and the decryption key Kd as parameters.
Secret-key Cryptography (symmetric encryption)
An algorithm in which each letter is replaced by a different letter. For example, all As are replaced by Zs, all Bs by Ys, all Cs by Xs and so on.
Plaintext: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Ciphertext: Z Y X W V U T S R Q P O N M L K J I H G F E D C B A
This system is called monoalphabetic sustitution, where the key is the string of 26-letters alphabet. In the above example the encryption key is ZYXWVUTSRQPONMLKJIHFEDCBA, the plaintext HELLO would become the ciphertext SVOOL.
Advantages:
- High speed
- The size of the message decreases
- High speed
- The size of the message decreases
Disadvantages
- It is necessary that the receiver knows the decryption key
- It is necessary that the receiver knows the decryption key
- Is not possible use unsafe media for keys communication.
Public-key cryptography (Asymmetric encryption)
Uses different keys for encryption and decryption, and if you choose a good encryption key is almost impossible to find the decryption key.
This cryptography works so that everyone chooses a pair (public key, private key) and publish the public key which is the encryption key and the private key is the decryption key. To post a message, someone encrypts the message with the recipient’s public key, only the recipient has the private key so he is the only one who can decrypt the message.
Public-key cryptography (Asymmetric encryption)
Uses different keys for encryption and decryption, and if you choose a good encryption key is almost impossible to find the decryption key.
This cryptography works so that everyone chooses a pair (public key, private key) and publish the public key which is the encryption key and the private key is the decryption key. To post a message, someone encrypts the message with the recipient’s public key, only the recipient has the private key so he is the only one who can decrypt the message.
Provides
- Confidentiality
- Integrity
- Authentication
- Digital Signature
Here we add some pseudocode of how this can work
a = “xxx”;
b = encrypt_algorithm
ke = encrypt_key
t_ecrypt = b ( a, ke)
t_encrypt = send ( )
receive ( t_encrypt)
kd = decrypt_key
if (kd == true){
t_decrypt = b (t_encrypt, kd)
a = t_decrypt
}
else
{
print “you need the key to decrypt”
}
References
Operating systems (Andrew S. Tanenbaum)
PING
Ping (Pachet Internet Groper) tests the state of a host connection with one or more computers by sending ICMP (Internet Control Message Protocol) packets. For example, imagine that we have a ball and we throw it to someone in order to prove if he is awake, he returns the ball and we now know he is, if he doesn’t respond at this it means that he is not awake. This is how ping works. Ping works in network layer, it encapsulates the message into a packet and then sends it.
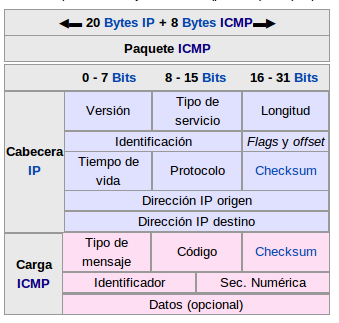
(In this image we show you how this packet is composed)
How does the ping work? In which port is it connected?. Ping works like ICMP, ICMP is part of the network layer (IP, routes, its objective is to make information to come from its origin to its destination), this layer is below the transport layer and works with routers. In the terminal, we can see ping by writing the command ping [ip adress], once that this is done, we can see constant messages of sent or lost packages.

Here we show you how a PING works
References
PING Image
(In this image we show you how this packet is composed)
How does the ping work? In which port is it connected?. Ping works like ICMP, ICMP is part of the network layer (IP, routes, its objective is to make information to come from its origin to its destination), this layer is below the transport layer and works with routers. In the terminal, we can see ping by writing the command ping [ip adress], once that this is done, we can see constant messages of sent or lost packages.
Here we show you how a PING works
///request
Ping()
ping.txt
validate()
verify structure
execute()
do ping->send
receive_ans(answer)
validate()
if answer = true{
echo “Connected”
}
else{
echo “Not Connected”
}
////anwer
receive_request()
validate(request)
if request = true{
answer->send
}
References
PING Image
Client-Server
A client server network is the one in which the clients are
connected to a server. This server provides special services (such as web
servers or FTP servers) to other machines or clients.
For example, when you are accessing a web page, the page is
providing a server, while your machine, on the other hand, is providing no
services, therefore it’s a client.
A machine may be both a server and a client. It can perform
different tasks as a client and as a server. For example, a server can also
have software running on it that allows it to act as a web server, an e-mail
server and a FTP server.
The one that receives is know as a server, and the one that
sends a demand is the client.
In a chat we can also clients connected to a server.
A server can listen for incoming calls or messages from all
the connected clients and broadcast them. When the client know the IP adress of
the server it can connect to the server in any PC.
The client can send messages to a server, and to the
connected clients. It also views all the messages.
Sockets
allow the implementation of a client-server model. Communication must be
started by one of the clients. The server waits for the client to start the
communication.
A socket is
a process or an existing thread in the client and server machine, it allows the client and server to read and
write information.
lunes, 14 de noviembre de 2011
Networking
A network is a
group of devices interconnected with each other in order to share information,
files, and resources. In order to make these operations we must have an
operating system controlling them.
In a distributed system, unlike a
multiprocessor system, processors dont share either a memory nor a clock, they
communicate through buses, telephone lines or some other communication
networks. In this system processors can be also called host, site or nodes.
When a system has data to send to
another system, the sending system segments the data and adds header bytes to
each segment, the resulting packages of information are know as packets.
A protocol defines the format and the order of messages
exchanges between two or more communicating entities, as well as the actions
taken on the transmission and/or receipt of a message or other event.
Let´s
suppose we have 3 processes in different systems: A, B and C in a network. They
can be connected in different ways:
- Fully connected network: They are all directly linked
- Partially connected network: Only some of them are directly linked
- Hierarchical Network: They are in the form of a tree
- Star Network: One of the sites is connected to all of the other sites
- Ring Network: Each one of the site is connected to exactly two other sites
- Multiaccess bus network:They communicate directly with each other through a shared link
- Hybrid Networks: Different networks connected together
References
Computer Networking (Kurose Ross)
Suscribirse a:
Entradas (Atom)

























